Checking the Status of KernelCare Enterprise Patches
TuxCare’s KernelCare Enterprise provides live patches for various enterprise-grade Linux distributions. Preparing patches for each new CVE has to account for each of those distributions’ particular quirks and configurations, so the release timing for each may be slightly different. Let’s look at the whole process and how you can follow along with current development.
The TL;DR version:
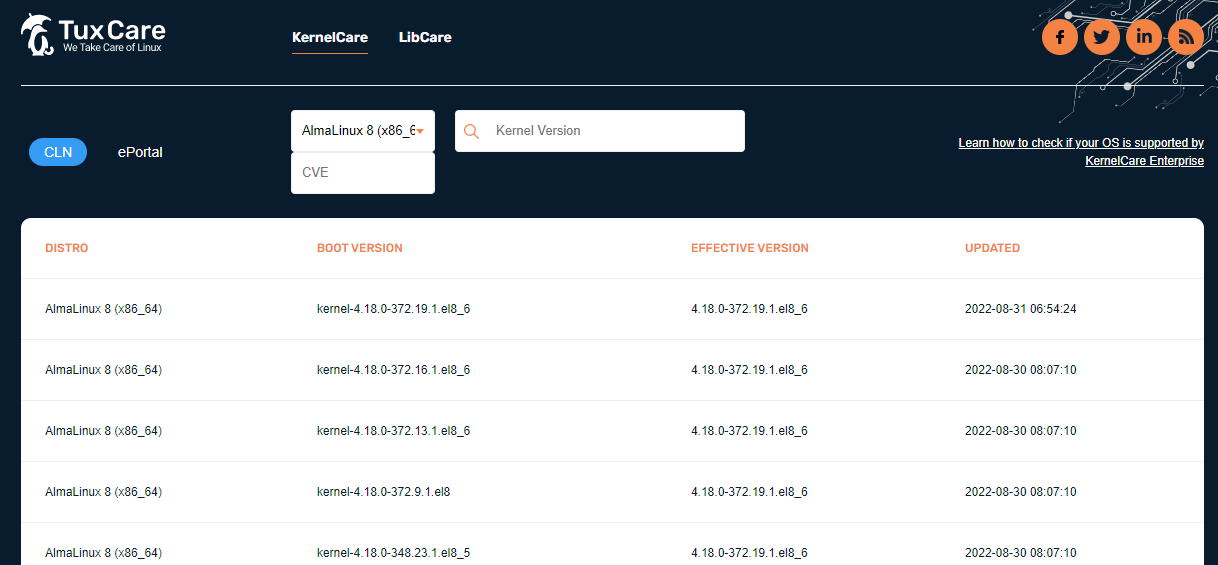
Check for supported kernel and distribution here: https://patches.kernelcare.com/
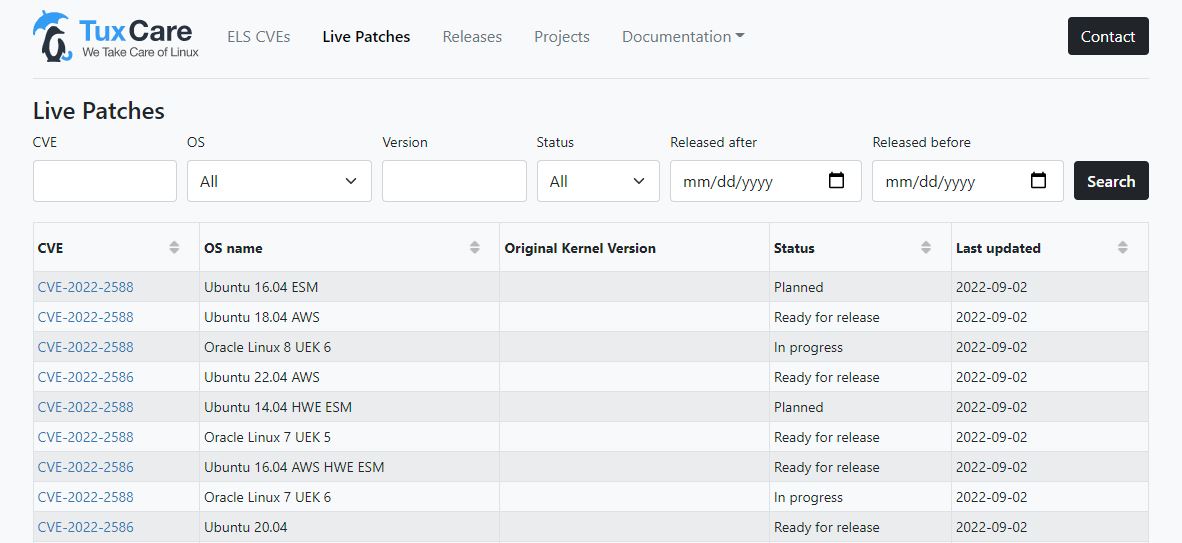
Check for specific CVE status here: https://cve.tuxcare.com/live
How to determine if KernelCare Enterprise supports a specific kernel from a specific distribution?
The information about supported distributions and kernel versions on each of those distributions is shown here: https://patches.kernelcare.com/
This information is automatically compiled from the build pipeline, which is always the most up-to-date information.
As new kernel versions are introduced in distribution, we will add them to our supported list as soon as all the automation tools that support the build infrastructure are tested and verified to support it correctly.
This is a quick process, usually a few days, but sometimes new kernel versions have new configuration options or some other quirks that require more extensive work to support, and that will add some more time before those are listed.
What is the current status for a given CVE? When will the patches for it be released?
The up-to-date information regarding specific CVE patches can be found at https://cve.tuxcare.com/live .
A CVE status can be one of the following:
- In progress
Development work is underway. The time this process takes to complete depends on the complexity of the patch, the difficulty in reproducing the security issue so that the testing suite correctly detects that the fix works correctly (or not).
- Ready for release
All the development work and testing have been completed and are packaged for release. This is the last step before actually making the patch available.
- Planned
The CVE has been analyzed and has been included in the development cycle. Some CVEs are so difficult to exploit or require such a complex series of operations that they are thought exercises, not security threats.
- Will not fix
The CVE was analyzed and determined to be irrelevant to supported distributions. For instance, it requires kernel parameters that are not shipped with the distribution or only affect a scarce piece of hardware that is not widely used, or no feasible exploit can be created. For example, if the exploit takes an outlandish amount of computing resources to trigger the vulnerability.
Just because a CVE is marked as “Will not fix” at a given point in time, as new information is disclosed, this may be reviewed.
Additionally, looking at the different CVE statuses for multiple distributions, it is possible to see that some distributions will have patches released sooner than others. This comes from the fact that the different kernels shipped with each distribution have different options defined, which in turn cause different interactions with the vulnerability and may require different approaches to fix it properly.



 Documentation
Documentation Login
Login