The Risks of an Open-Source Software Supply Chain
Open-source software has emerged as a crucial component of the software development ecosystem. It has gained widespread adoption among developers worldwide, owing to its benefits – such as cost-efficiency, adaptability, and community-driven support.
Access to pre-existing software components allows companies to boost their development processes and deliver their products to the market much faster. However, with the increasing usage of open-source packages in application development, there are mounting security challenges. This blog post discusses the challenges of securing an open-source supply chain and how to address them.
The Sweet Spot for Attackers
As the use of open source continues to grow, threat groups get the opportunity to exploit the software supply chain to access a wide range of targets that rely on it.
Cybercriminals understand that many organizations are unaware of the open-source software utilized in their systems and the vulnerabilities present within those components. Instead of spending a long time trying to hack into an organization’s custom code, hackers are using publicly available exploits to target a wide range of organizations and find systems with vulnerable open-source components to exploit.
Plus, one of the main reasons that attacks on open-source supply chains are so successful is the immense complexity of the dependency graphs.
The Jenga Effect
Every open-source package has its own unique supply chain and may rely on multiple third-party open-source libraries. These third-party libraries often depend on other libraries, resulting in a highly complex chain of interdependencies.
Considering the fact that popular libraries are widely used by many open-source packages, a single vulnerability in one of them can wreak havoc on the entire ecosystem. We’ve already seen this many times: from a vulnerability in the free Log4j logging library to one of the most recent cases when an open-source developer introduced a breaking code to his wildly popular npm package colors.
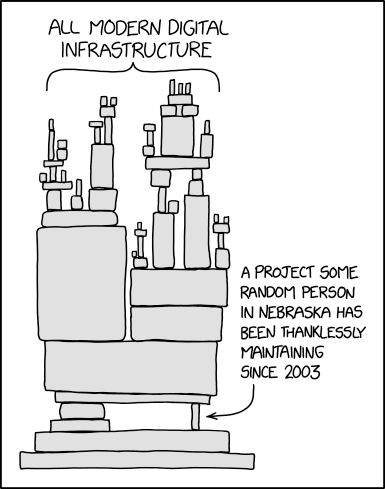
Source: https://xkcd.com/2347/
You Can’t Protect What You Can’t See
In a perfect scenario, engineering teams would maintain comprehensive documentation of the open-source software utilized within the organization – also known as a software bill of materials. They would update this documentation each time a new dependency is added, allowing for the easy identification of where and if a particular library, such as log4j, is being used.
This documentation would also help to discover unmaintained packages in a timely manner, as they may introduce additional security risks. However, it takes a lot of work for developers to practice documenting software components consistently. At the same time, security teams in many organizations need more visibility into the dependencies their companies are using.
Missing Your Time-to-Market
Considering the complexity of open-source software dependency chains, keeping up with all its latest vulnerability fixes and driving innovation all at the same time becomes almost mission impossible.
To ensure security and legal compliance, companies started actively implementing formal approval processes for introducing new open-source components. In some cases, getting new components approved can take up to a month or more.
At the same time, product managers who must carefully balance their development resources to maintain competitiveness struggle to prioritize new features over the increasing number of vulnerabilities affecting their applications. All this can cause a significant delay in development and, in turn, in the time-to-market, which can be critical and lead to lost opportunities at the very least.
The Way to Go
One of the potential solutions to the challenges organizations face with open-source software supply chain security is the practice of centrally managing a repository of pre-approved and continuously secured open-source components. You can establish it yourself or partner with a trusted vendor who will establish and manage it for you.
Gaining access to such a repository will enable you to:
- Minimize security risk by ensuring that your dependencies are free from vulnerabilities and malicious code
- Gain control over your dependency graph with an assured Software Bill of Materials provided for each package
- Comply with your patching policy and regulatory requirements by establishing reliable SLAs for security fixes
- Accelerate your time-to-market by eliminating excessive approval processes and reducing your technical debt
A single trusted repository of vetted open-source packages will allow you to continue innovating while automatically maintaining the security of your applications. If you are interested in securing your Java supply chain, get access to our free Java repository now.



 Documentation
Documentation Login
Login



